You might asking yourself, what the heck is DNS Flag Day anyways? Before you go Google it yourself, let me break it down for you. On or around February 1st, 2019 major DNS service providers are going to start enforcing EDNS. Which DNS service providers you ask?

…and what is EDNS? Extension Mechanisms for DNS (EDNS aka EDNS0) essentially allows for larger packet sizes, 512 bytes being this traditional size for DNS. By increasing it to 4096*, EDNS allows for the ability to inject client IP information which is ideal for CDNs (cough cough CloudFlare) or to support DNSSEC. DNSSEC (Domain Name System Security Extension) was designed to protect applications (and caching resolvers serving those applications) from using forged or manipulated DNS data, such as that created by DNS cache poisoning.
*Size matters in this case.
Many NGFWs may block traffic as they are expecting the packet to be 512 bytes and may drop. You may need to add an additional firewall rule to permit DNS packet that are =< 4096 bytes.
Sadly this spec has been around since 1999, so now the giants have drawn the line in the sand, support it as of 02/01/2019 or not, we don’t care. If you don’t, this is how it will look for your customer, users, and/or contractors that rely on 3rd party DNS services:
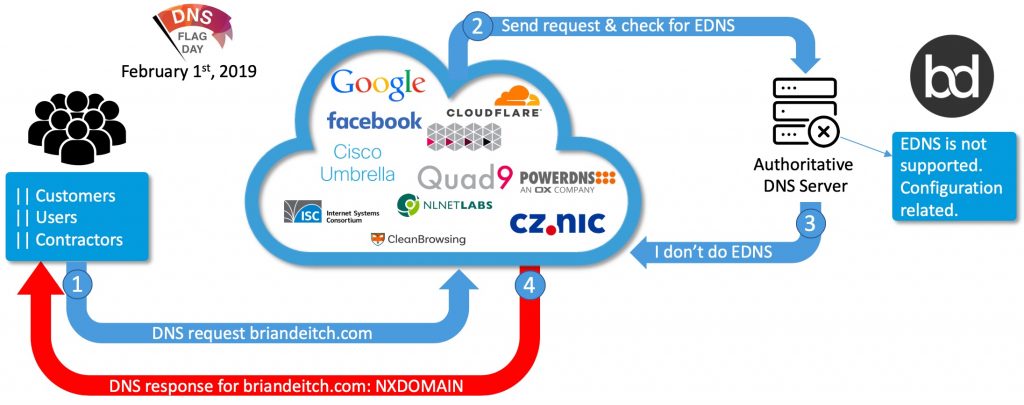
I think we can all agree that doing this on a Friday is a terrible idea. Want to piss off people who work in IT? Don’t socialize a change that could impact many people and make sure that the people who can troubleshoot it and fix it, work through the weekend. They love that kinda stuff. About as much as they like when their puppy eats a shoe lace and they have to pull it out of their butthole.
Continue reading DNS Flag Day: Are you ready?