While I can think of a hundred other things to do with my phone, crypto mining has never been one of them. Which is why I was surprised to see in June of this year, Apple banned crypto mining apps from the App Store. Who knew crypto mining on iOS was even a thing?
There has been a lot said regarding the security of the iOS platform, especially when compared to Android. While iOS does an amazing job sandboxing applications and preventing your iPhone from becoming the next biggest botnet, I was surprised to see some crypto mining from inside my house…and not the cool kind of crypto mining that puts coin in my pocket. This was malware running on a system inside my house.
From a network landscape perspective at my house, everything is locked down depending on two factors:
- Can I MiTM SSL/TLS?
- Can I enforce authentication?
If I can inspect your SSL/TLS connection and force the device to authenticate, I will throw that device on a separate network called “trust”. At my house, we are Apple fanboys loyalists users.

For everything else, guests included, you get to hang out in the “untrust” network. What devices do I keep in the untrust?
- Guests
- Home Automation
- IP Camera
- Smart TVs
- Printers
- Gaming Systems
- IoT
Based on the limited information you have on my home network, if I were to tell you that I saw crypto mining in July 2018 at my house, which network would you suspect, trust or untrust?

Remember, you have to answer in the form of a question!

If you guessed the untrust network, that was my guess as well. Unfortunately, we are both wrong. I was surprised to see that the traffic had originated from the trust network!
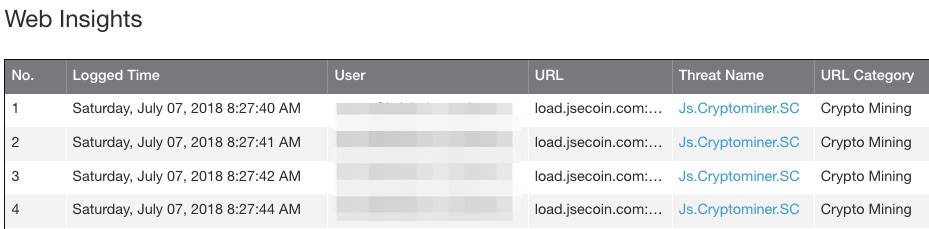
Let’s dig into this by modifying the filters to show all activity, not just the blocks during that time period.
As you can see below, the user was playing an online game when the crypto mining occurred. The 403 response was from Zscaler, essentially throwing a block page and preventing the crypto mining from being downloaded and executed on the mobile device.
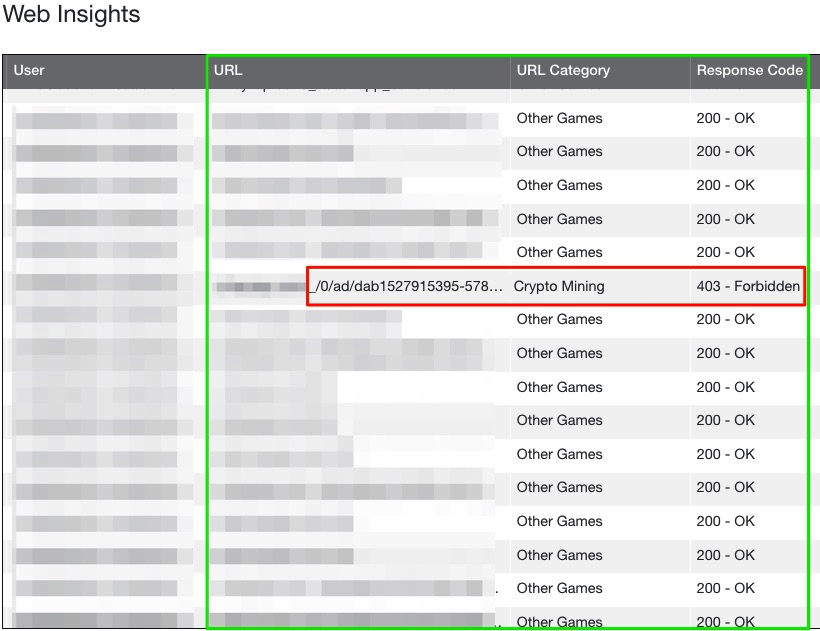
This traffic was originating from my sons iPhone and I purposely masked the URL as I didn’t want to give away the name of the game as I don’t believe they had anything to do with it. I understand the data is pretty compelling here, right smack in the middle of the game, there is an attempt to run the crypto mining. Upon further inspection of the device, my ability to reproduce the crypto mining traffic wasn’t as easy as opening the app and playing.. It turns out, the crypto mining only occurred when the game would run in-game advertisements (malvertising) (around 30 seconds or so) but not every time. Looking back at the article I referenced at the beginning of this post:
Apple has added new language to its App Store review guidelines related to cryptocurrency. Under the Hardware Compatibility section, Apple now states that “apps, including any third party advertisements displayed within them, may not run unrelated background processes, such as cryptocurrency mining.”
A month after Apple banned all crypto mining apps from the App Store, logs indicate that it was still going on. That didn’t stop the bad guys…as we all know, if there is a will, there is a way. Instead of creating a crypto mining app, how about embedding it in some ads? Write the crypto mining malware in JavaScript, find a fun app, and load it from there. If you think about it, these ads only play for a couple of seconds so it can’t be that lucrative. But if you were to scale up operations by targeting an application with a huge user base, like Clash of Clans, Fortnite, PUBG, etc (none of which were used to run crypto mining at my house), it might make sense. Furthermore, perhaps the JavaScript can be a bit more persistent and run in the back-ground with some type of evasion technique for the iOS sandbox. In my scenario, persistence doesn’t appear to be the case when the app reached out, the URL hosting the malicious mining JavaScript was blocked by my Zscaler Proxy. Which begs the question, ‘Could it have been persistent?’ After reviewing this article about the malware, load.jsecoin.com, it does contain persistence properties. Based on my research, Safari for iOS would not have been impacted long term, essentially only when the ads were playing. Other platforms such as Android, IE, Firefox, Chrome, etc. required several steps to remove the malware.
It is worth noting that I have not seen any more crypto mining on my home network (only 7 users and 43 IoT devices) since late July 2018 however that does not mean the problem is fixed.
Zscaler Security Research Anti-Coinminer Mining Campaign 08/2018
Checkpoint 400% increase crypto mining attacks against Apple Devices 09/2018
Phys.org Hackers Target Smartphones to Mine Cryptocurrencies 08/2018
So there you have it. Regardless of the platform you running, the bad guys are going to figure out a way to compromised you one way or another.
What are you doing to protect yourself and the enterprise?
Regards,
BD

