If you haven’t already done so, you should read the Verizon Data Breach Investigations Report that they publish annually. In the 2018 Verizon DBIR, it is chock-full of good reading around the specifics of breaches in 2017 and provides an insight to the Who, How, Why, What, and When. In the report you can read about the internal threat actors down to how malware was distributed. In all, Verizon has dotted all the I’s and crossed all of the T’s and provided you visibility into 53,000 incidents and 2,216 confirmed breaches across all verticals in 2017. Historically I have used these reports to help educate myself and my customers on the threat landscape as well as leverage the information to help justify spend on security related products, tools, or services to help keep the enterprise safe.
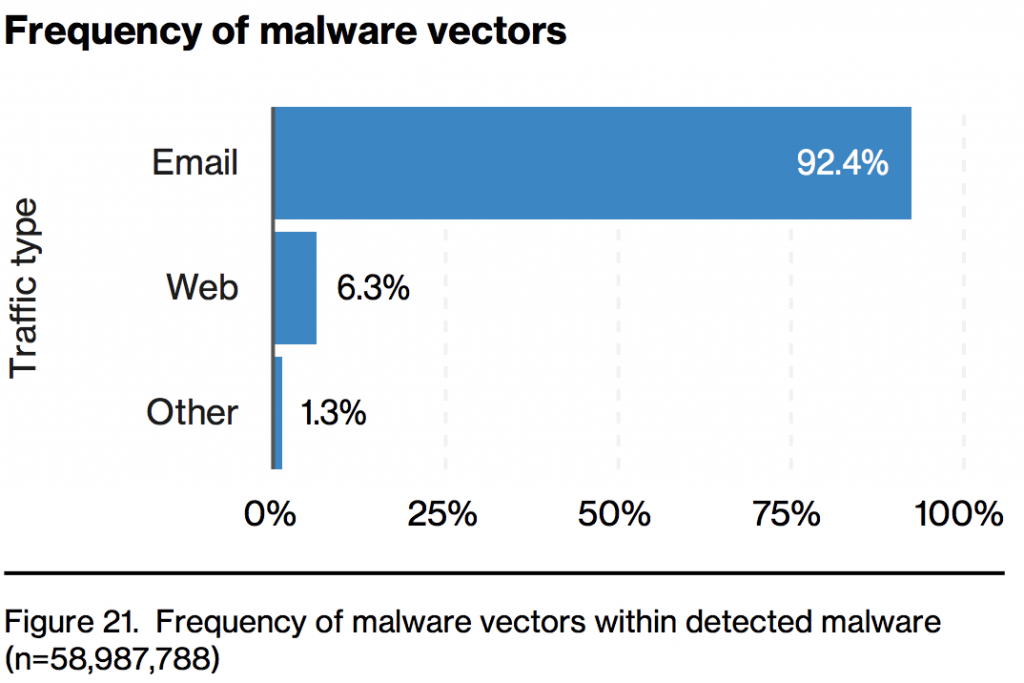
While reading the report, the sections regarding malware (ransomware included) stood out to me. Why? Well come on, you would think by 2017 will all of the security tools deployed that malware, even 0-day, wouldn’t be an issue but it still is. On pages 17/18, the report discusses the frequency of malware vectors, or basically how malware is distributed.
Continue reading Caught on tape: Malware Distribution Techniques




