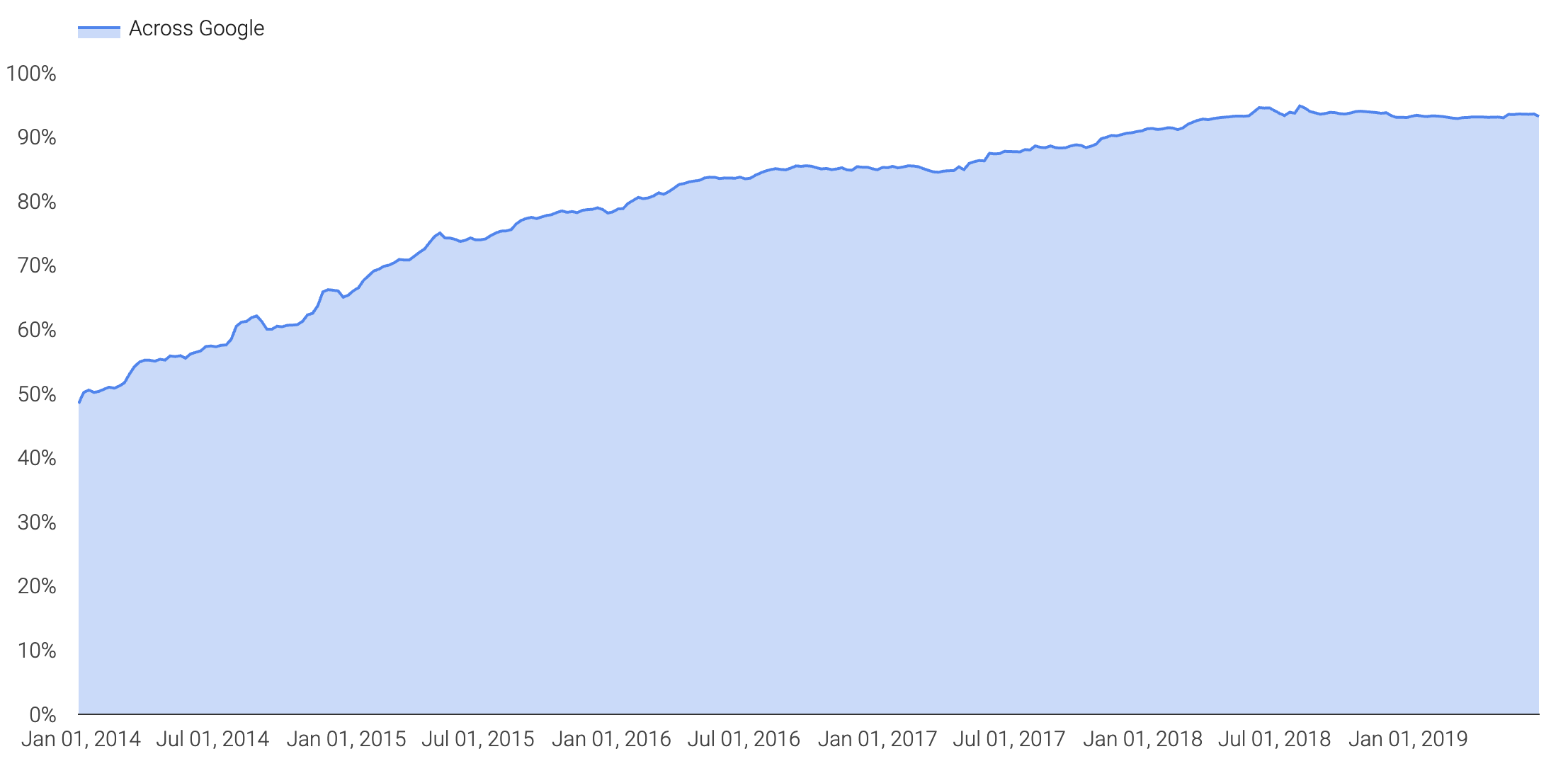
Thanks to wikileaks, HTTPS Everywhere, and Let’s Encrypt, adoption of encryption (HTTPS) has skyrocketed in the past couple of years. According to the Google Transparency Report, they are seeing as much as 90%+ adoption with traffic headed to google:
While I love my privacy and fully support end to end encryption, encryption, specifically TLS 1.2 (with PFS) and above, straight up blinds me from a packet capture perspective. When a destination website support TLS 1.2 or greater, I am no longer able to record traffic, open wireshark and see what is going on past L4.

Troubleshooting the web in todays world without application layer data (L7) is straight up useless. Wireshark has become a tool to validate connectivity; source/destination port/protocol–lame. If you are a network monkey, I am sure you are thrilled with that level of visibility but trust there is much more going on at L7. Today, most people actually rely on headers captures or Fiddler to see what is going on at L7 but let me tell you, I miss wireshark.
Spoiler alert, you can decrypt TLS with PFS (ECC keys) and it doesn’t require MiTM:
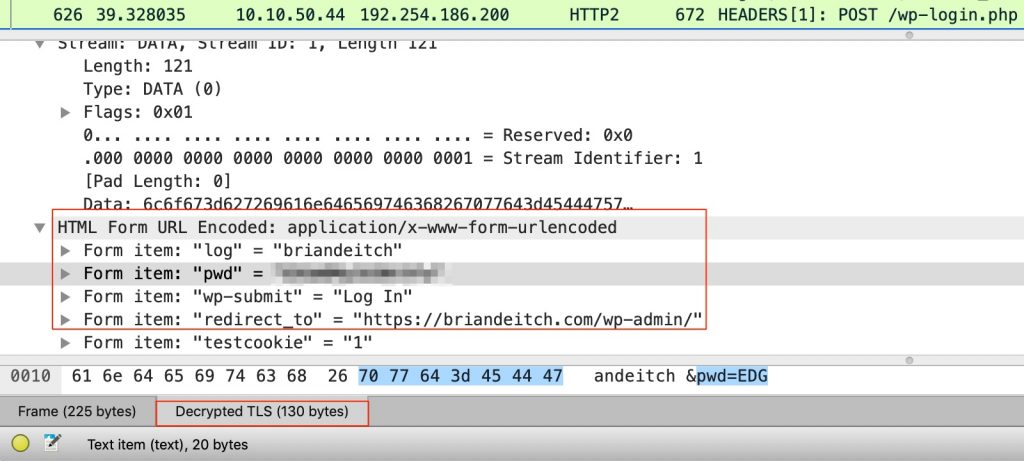
Yup, that’s a pcap opened in wireshark when I logged into the admin portal of this blog. And for what it’s worth, SSL Labs gives this blog an A+ for security so you have piece of mind that my capture wasn’t picking up clear text traffic. Note the form items “log” and “pwd”; that’s the username/password combination I used to log in. But also notice Decrypted TLS (130 bytes) as well 😉
Continue reading Cracking open that TLS connection