Raise your hand if you’re using any or all of these technologies:
- NGFW
- IPS/IDS
- URL Filter
- Antivirus
- DLP
- Sandbox
- VPN
- DDoS Mitigation

Pretty much all of us, right? Now raise your hand if you are decrypting SSL/TLS outbound.

While HTTP/2 doesn’t require SSL/TLS, it will use it by default if it is available. Oh by the way, all modern browsers have supported HTTP/2 since January of 2016. Factor in the efforts of Let’s Encrypt, the adoption of SSL/TLS has skyrocketed in the past few years and will continue to grow. Hell, even this shitty blog is using TLS 🙂 If you aren’t decrypting SSL/TLS you have to ask yourself, what good is my NGFW, IPS, Antivirus, etc if I am completely blind to it? The answer is simple, it isn’t good, in fact it’s terrible. You are bound by the constraints of legacy security, source/destination and ports. It’s like locking a screen door. It will keep the flies out but it won’t stop any real threats.
Certainly all of your legacy security vendors will tell you that they can decrypt SSL/TLS but it comes at a significant cost to you. So what does that mean to you? Time to refresh all of your gear but this time you need to buy bigger boxes, in some cases the legacy security appliance you’re looking at can scale to your needs so you’re forced to buy a load balancer, and lastly bust your your crystal ball because whatever you buy needs to last for the next 3-5 years minimum. Oh yeah, I forgot, your entire business runs through the DMZ and your upgrades better not cause any service disruption and we better be blocking (ROI baby) the bad guys immediately. Just go to the business, request a huge capex, ask for professional services, training, and new head count. Piece of cake right?

That is the old way of thinking and for many of us, that was our reality for the past decade. The business is changing how we do security and we must align to these objectives:
Fast Response Time
- Higher productivity
- Prioritize business apps
- Empower users to use cloud apps
Reduced Risk
- Secure all users, on all devices, everywhere
- Consistent policy and protection
- Always up-to-date
IT Simplification
- Consolidate point products and simply IT
- Cloud-enabled network
- Rapid deployment
Value
- No Capex, elastic subscription fee
- Reduce opex
- Reduce MPLS costs
Traditional security doesn’t meet todays business needs and demands.

As it turns out, Zscaler is a modern access and security architecture that was built from the ground up and founded in the cloud. That’s right, you heard me correctly. Zscaler has the ability to inspect every packet across all protocols, decrypt SSL/TLS, and perform all of the challenging L7 inspections such as NGFW, IPS, DLP, Sandboxing, URL Filtering, DNS, and Antivirus. You might be thinking, too good to be true, right? I know that’s what I thought. The proof is in the pudding and I would like to share with you 3 real-time metrics (I am having issues embedding the content in real time. Below are screen shots take on 06/16 at 1130MST. You can view the real time dash board here.). Before we dive into the metrics here is some perspective. The data you are about to read comes from 100 data centers over 5 continents with a user base well over 16 million.
You move a lot of data? We move more. Jump on your busiest security appliance and tell me how many full L7 transactions you are doing right now. Now look at this:
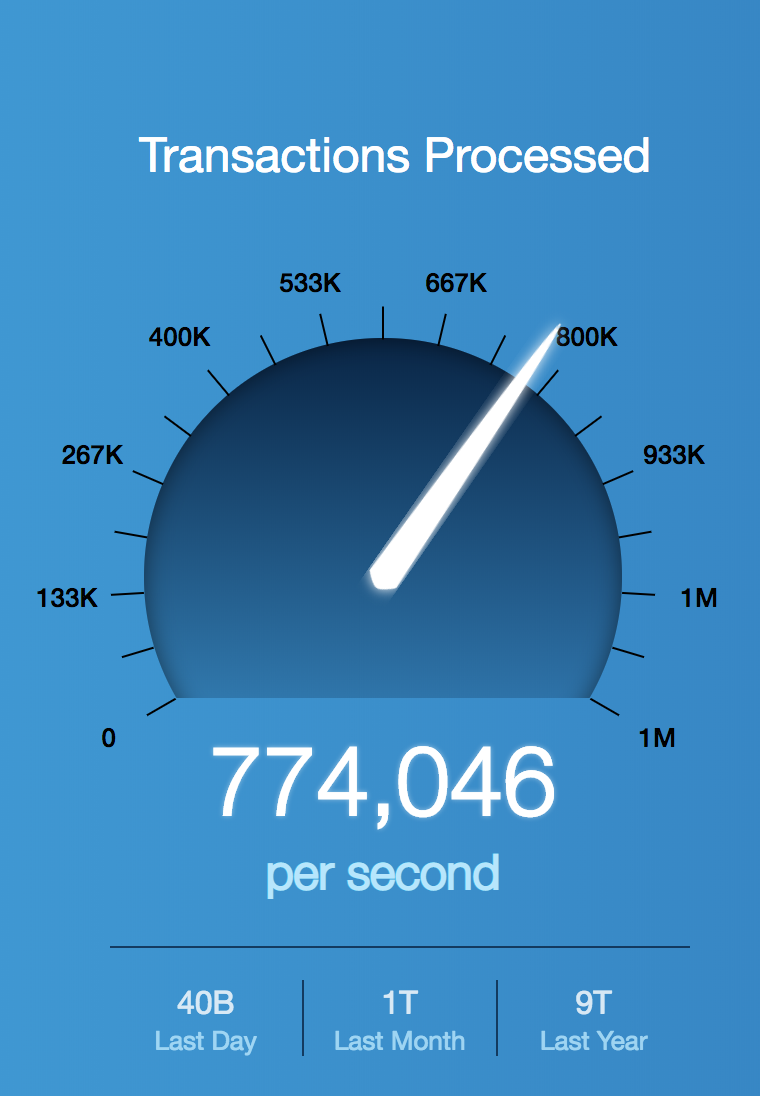
Yup, that’s 40+ Billion requests handled per day in our cloud. Okay, same exercise this time but tell me how many polices you are dealing with? Now take a peak at Zscaler:
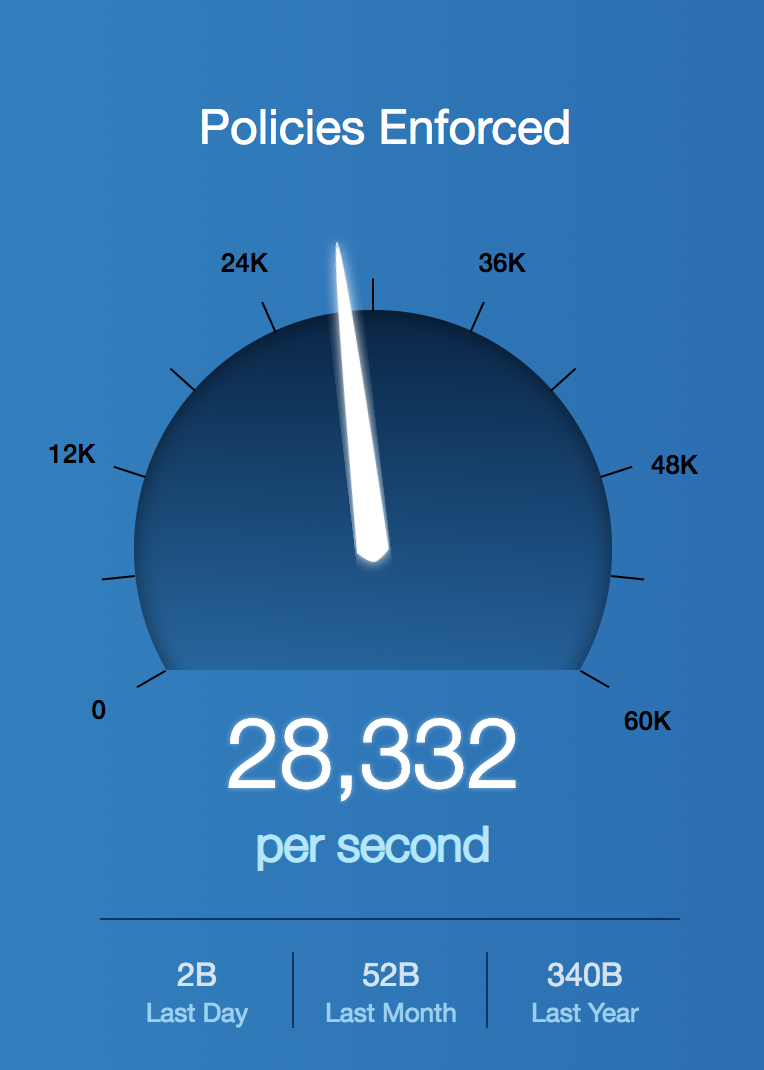
And I bet you thought the number of policies you manage was a lot. So we’ve established that Zscaler is seeing a ton of traffic, managing and executing policies but are we blocking anything? Absolutely. If you were to log into your SEIM and pull the number of threats blocked in the past year I bet it would be a fraction of the threats that Zscaler blocks in a single day. Check it out:
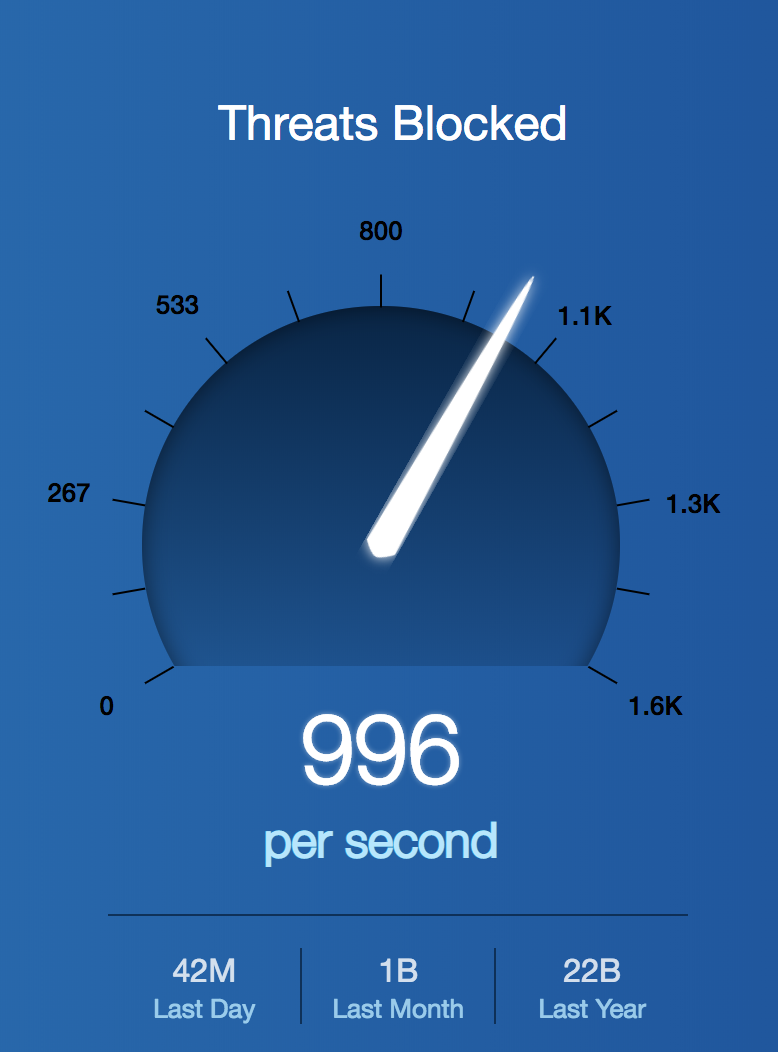
Go ahead, do the double check, squint your eyes, those are real numbers. Zscaler is rejecting the bad guys like a kid rejects a birthday present from Mom’s new boyfriend. Please remember, there are 16 million users on the system each day and it’s business as usual for them with one exception; there is no compromise in security. Now that’s executing security at scale if you ask me.
So ask yourself, what level of effort and cost are you willing to accept to do this yourself with legacy security appliances? Is this something that you can do in the next 6, 12, 18, or 24 months? Maybe it’s time to look at cloud security company that has already done the heavy lifting and proven themselves with over 16 million users.
Regards,
BD

